Although the number of active Tor users number in the millions, not everyone is familiar with the Tor Project. So this is part one of a multi-part series on the various tools Tor provides. Today, we will look at the Tor browser. The next 4 articles will focus on :
How to set up your own bridge relay to hinder ISP’s from blocking Tor browser traffic. Using the secure Linux-based operating system Tails, developed by Tor. Using the secure instant messaging platform Tor Messenger. Using Torbirdy, which enhances the security of Thunderbird email users.
As each article is published on the site, the bullet points above will be updated with the direct links. There are other things in the Tor Project, but it is not necessary at the beginning to know about these. These are more advanced topics, and as with any subject, you need to get the basics down first.
What Is Tor?
Tor was launched in 2002 and was originally developed by the US Navy. It therefore got a lot of its funding from the US Government, but it eventually had other financial backers such as the Electronic Frontier Foundation. Its original aim was to protect internet users’ privacy from corporations, which is ironic considering that today the purpose of Tor has done a total 180 degrees and is now used to protect people from the government, the very entity that funded Tor in the first place! Needless to say, the US Government is now not a fan of Tor, as it has taken on a life of its own, and law enforcement find themselves frustrated by encrypted criminal activity. It is now under relentless attack from agencies such as the US’s National Security Agency, and the UK’s Government Communications Headquarters (GCHQ), in a bid to crack it.
Tor is used by many different groups of people, but it unfairly gets a bad rap because most people associate Tor with its criminal associations – the Dark Web, Silk Road, drug dealers, assassins for hire, and the like. But there are MANY legitimate uses for Tor too, which many people overlook.
It is used by journalists to protect their sources and to protect themselves from government interference. It is used by activists and campaigners. It is used in totalitarian countries and regions such as China, Russia, and the Middle East to enable its citizens to criticize their government and other authorities such as the police, the military, and the courts. Most of all, it is increasingly being used by ordinary Internet users like you and me to make sure we are not being tracked and traced online. It can conceal your location and cloak your browsing habits.
Tor HAS been breached once by the FBI to bust a child porn network. But on the whole, it is still considered extremely secure.
The Tor Browser
The main platform of Tor is its browser, which is available for Windows, MacOS, and Linux (there are also Android and iOS equivalents which we will look at later). It is modified from the Mozilla Firefox browser, and it acts like a virtual private network. Tor Internet traffic first gets re-routed through several public Tor servers, each one not knowing where the next server will be. But as these servers become more well-known to ISP’s around the world, it becomes easier to block them. So in an attempt to circumvent the blocking of public Tor servers, your Tor browser can instead be redirected to a relay somewhere the world. These relays are not publicly registered so they are much harder to trace (we will be looking at this in more detail in the next article). The downside to using Tor is that your browsing speed is MUCH slower than normal, as your web traffic has to jump through a few extra hoops than it usually would. There are also a couple of things you need to remember, as Tor is not your usual browsing experience.
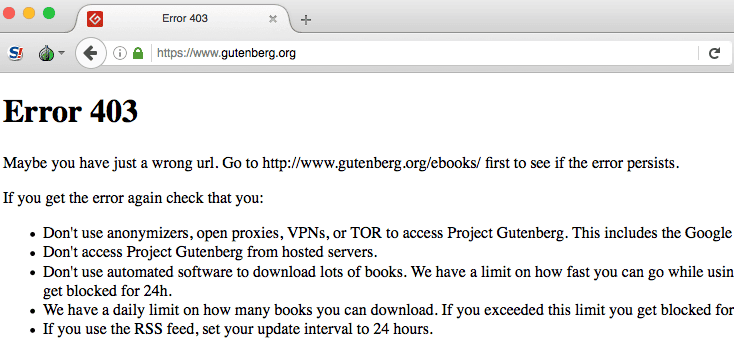
Plugins such as Flash, RealPlayer, and Quicktime are blocked, as they are considered to be unsafe. Since Tor is a modified Firefox browser, you could technically use Firefox plugins. But Tor strongly recommends against doing this, as it can’t guarantee the trustworthiness and security of each plugin. It does however have the EFF’s plugin, HTTPS Everywhere, automatically installed to ensure everything is redirected through secure connections. Some websites outright reject Tor traffic. One example is Project Gutenberg, which returns this error message.
Starting Up Tor
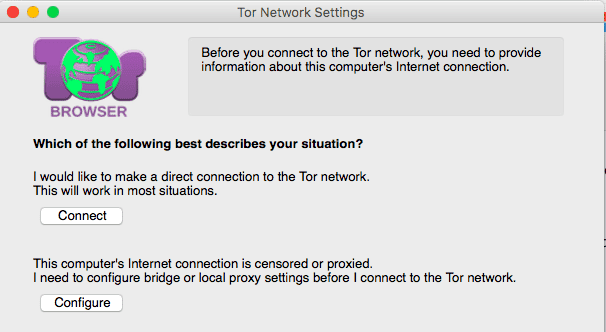
You can download the browser for free here. Install it like you would with any other program, and start it up. You will first see this.
I have never needed option number 2. Most of the time, option 1 is all you will need, so go ahead and click the “connect” button. It will then tell you that it is connecting to the Tor Network. It virtually never takes “several minutes”. It is much faster than that.
Then you will see the browser window open, ready for browsing. At the top, you will see the IP address you are now on (although I have blanked it out in the screenshot).
Browsing Websites
As I previously mentioned, some websites will block Tor. Some people have reported issues with Wikipedia, although it was working when I tested it. This StackExchange page details other problematic websites on Tor such as Vimeo, Github, Cloudflare, and curiously, HealthCare.gov! Even Google sometimes hiccups when you search for something, getting you to complete a CAPTCHA to prove you’re human. Other than that, you can browse at will.
Onion Sites & The Dark Web
I am not going to go into this in detail today. I intend leaving this subject for a later date as it is so in-depth. Suffice to say the Dark Web is a whole other Internet which is not indexed by any conventional search engine. These sites are called “Onion” and usually have scrambled URLs. This is the problem about browsing Onion sites – since the URLs are usually scrambled, and sites go up and down all the time, there are very few reliable directories listing these sites, as they go out of date very quickly. It is not only criminals that use the Dark Web. Many top websites also have Onion versions. Facebook’s is https://facebookcorewwwi.onion/ and is only accessible through Tor. Activists, bloggers, and journalists in oppressed countries also maintain Onion sites to hide their online activity, giving out the URL to a trusted select few.
Other Versions
As well as versions for Windows and MacOS, there are other versions of the Tor browser you should seriously consider.
Windows Portable Version
For the truly paranoid, you can have a portable version for Windows, which can be run off a USB stick. To save it as a portable version, install it on the USB stick, instead of installing it on your computer when you first run the program. You can also download it from Portable Apps, which is usually a very trustworthy site. However, to be on the safe side, I would recommend only downloading it from the Tor Project website. That way, you know you’re getting the real thing.
iOS
The best option for both the iPhone and iPad is the Onion Browser (other apps get bad reviews). This is a truly fantastic browser and I use it all the time. It is also free and open-source. Cookies, cache, and Internet history can be wiped with a click. I have had absolutely no issues with Onion Browser at all, and strongly recommend it to all iOS users.
Android
There are two good options for Android, both made by the Guardian Project, a EFF-like privacy software organization. Their Android apps are called Orbot and Orfox (sounds like twin brothers). Both are free and highly regarded, but the one I hear the most about (and gets the most praise) is Orbot. Each of the two pages will give you the various features of the two browsers, but it is clear at first glance that Orbot is the dominant successful one. It has private chat messaging, works with the official Twitter app, and any app can be re-routed through Orbot if that app has a proxy feature.
Conclusion
I hope this article has given you a good understanding of the Tor browser, and that it has encouraged you to give it a try. Next up is how to run your own Tor relay. Stay tuned for that.